Multi-Layer Security, SPOC and Shaping Way Ahead for Deploying C2 Hubs Empowering Integratability
In my article on “Standing C2 on its Head,” argued that C2 systems are no longer commodities added platform by platform; they are the operating infrastructure within which platforms find their role within a scalable, tailorable combat force.
But how best to build out such an operating infrastructure based on the force we have, rather than envisaging a new world in 2030?
Which networks deliver the best information, at the right time for the most effective actions?
This is associated with the challenge of providing access to a wider range of networks for crisis management across the spectrum of conflict, and which operate with a wide variety of security requirements, protocols and caveats.
In my previous article on C2/ISR enablement, I highlighted the impact of the F-35 and the CNI system in shaping a new way ahead.
In that article I underscored the solution set involved in CNI allowing the F-35 to fight as a Wolfpack.
But the technology involved with the F-35 solution set, although specific in many ways to that platform, has opened a way ahead to bring new C2/ISR enablement to the wider combat force.
This approach leverages the unique security solution built into the F-35 approach, and leverages as well the SWaP learning curve evident in the F-35 global enterprise.
But while leveraging their experience with CNI, the Northrop Grumman approach to software upgradeable C2 hubs (radios if you wish) provides for a wider range of solution sets than are available if one was focused on the low latency requirements approach as the baseline requirement.
This approach functions as the second epicenter within Northrop Grumman to shaping a new way ahead to C2/ISR integratability for the distributed combat force.
This second epicenter of Northrop Grumman’s approach to shaping C2/ISR solutions for the multi-domain force takes elements of the F-35 solution but sets in motion a different trajectory to shaping a solution set.
Theresa Hitchens of Breaking Defense provided her description of the Northrop Grumman approach to innovation in the radio domain in terms of their new Software Programmable Open Mission Systems (OMS) Compliant (known as SPOC) radio terminal.
She noted: “Northrop Grumman has won a $14.5 million chance to prove to the Air Force that its design for a new radio would allow operators to use multiple US and allied data links and help the service realize its plans for the Advanced Battle Management System (ABMS).
“Importantly, the new Software Programmable Open Mission Systems (OMS) Compliant (known as SPOC) radio terminal will allow the Air Force to rapidly develop and prototype upgrades or change or to third-party contractors to do so. In other words, the software code is not proprietary to Northrop Grumman….
“As Breaking Defense readers know, the Air Force — and DoD writ large — continues to struggle to allow myriad communications terminals designed for one platform to talk to other weapon systems….The Northrop Grumman radio will provide one-stop access to four types of radio frequency communications widely used by all services and some allies for air-to-air and air-to-ground communications:
“Link-16“ CMN-4, an upgrade to the ubiquitous communications link used by military aircraft, ships, and ground forces to exchange tactical information in near-real time, developed by Naval Information Warfare Systems Command;
Common Data Link (CDL), one of the oldest (dating from the 1990s) secure military communications protocols that serves as a primary link for sharing imagery and signals intelligence;
Multifunction Advanced Data Link (MADL), which Breaking Defense readers know is the hard-to-detect waveform used by the stealthy F-35 Joint Strike Fighter, which can unfortunately only talk to other F-35s; and,
Multi User Objective System (MUOS), the narrowband, ultra-high frequency satellite communications network developed by the Navy, but used by all the services for mobile communications.
“The open architecture networking terminal offers numerous benefits” to the Air Force, according to Northrop Grumman, “including opening the F-35 communications, navigation and identification (CNI) system to third-party developers; ownership of Link 16 development; sharing of intelligence, surveillance and reconnaissance information over a common data link; and Mobile User Objective System beyond line of sight capability.”
Hitchens has provided a good analysis of the Air Force contract win for Northrop Grumman.
But underlying this programmatic effort is what I am referring to as the second epicenter for Northrop Grumman in working C2/ISR connectivity for the combat force.
The underlying capability built into the F-35 is carried over into the SPOC networking hub approach.
The system operates on the basis of a multilevel security architecture.
Rather than having each card in the box working a separate network with its own logistics and hardware requirements to be met on the platform on which it is operating, the cards in the network hub box can leverage common logistics and hardware.
MLS, which is a government owned capability managed by Northrop Grumman, can work across the card infrastructure to shape common delivery processes which can differentiate among the data to allow for the maximum allowable for security policies in place to deliver data to an authorized user.
MLS is incorporated at the processor level which allows for a modular, scalable architecture to manage networks and the data which they provide.
What the MLS architecture allows is for the use of networks to provide information and to make C2 decisions across the joint force or a coalition.
What it allows is for the kind of force aggregation which is required for full spectrum management.
A force could go out and conduct its current mission and switch the next day to a new mission with different force components involved in that mission.
Ultimately, one would one to be able to be able, in real time, to reconfigure all of your hardware for the required set of security caveats.
With the MLS architecture because the caveats can all can run on the same processor, and they all use the same memory space, and are transported over the same buses in the network box, subject to a limitation of the processing throughput, one can put as many caveats as you want into that system.
This architecture is the foundation of the SPOC approach, and is morphed from the CNI approach.
But whereas the cards being inserted into the CNI hardware are optimized for low latency communication and low observable operations, the cards which can be inserted into the SPOC “box” can focus on a wide range of networks providing information for C2 decisions across the spectrum of conflict.
The SPOC “box” can accommodate a wide range of cards, and notably ones not built by Northrop Grumman itself or, for that matter, by only U.S. vendors.
With the MLS architecture, SWaP needs are highlighted and met.
Because each card in the networking box does not need its own subsystem of support from the platform, real estate needed to operate the SPOC networking capability is significantly reduced.
Rather than having to operate multiple physical buses and processors separated in a network box, Northrop’s approach to MLS provides for separate applications and their data operating a multiple levels of security on a single processor.
And if one can work reconfiguration of communications across a spectrum of security, then one is able to deal more effectively with cyber war considerations as well.
As is already evident with regard to the F-35, the CNI allows for the F-35 global enterprise to work security caveats across the coalition. With SPOC, this is about working across the joint or coalition force, with similar adaptability built into the MLS architecture.
The MLS architecture is designed to achieve the maximum possible processing per watt which provides a foundation for shaping expanded capabilities as well.
Because this is a software governed system, there is a high potential for adaptability and code rewrite in response to the dynamics of change in the battlespace.
With a software-definable system, the capability to transition to a new radio type and a new frequency is facilitated, notably with the advent of broadband antennas, which allow for scalability and adaptability in the networking domain and it’s empowering of more flexible C2 and C2 at the tactical edge.
In short, the two epicenters of effort drive change in networking flexibility, capabilities and viabilities in dealing with full spectrum crisis management.
With CNI, one is working the challenge of low latency communications for a low observable platform working within unique combat clusters of F-35s.
With SPOC, one is working across the spectrum of conflict, and working to ensure that there are no digital orphans in the battlespace, and that integratability is possible across the broad-spectrum force.
A clear advantage of SPOC is providing other platforms to be interoperable with F-35 and new platforms that might have new LO waveforms.
In other words, even though one can conceive of the NG approach as being driven by two epicenters, they clearly provided cross-cutting leveraging in terms of technology, wave forms and security management.
What this allows is the strategic shift towards the 6th generation world in which networked sensors allow for the flow of data through networked systems to inform decision making for a distributed force which can morph as needed into an integrated force scaled to the effect needed to dominate or manage a crisis.
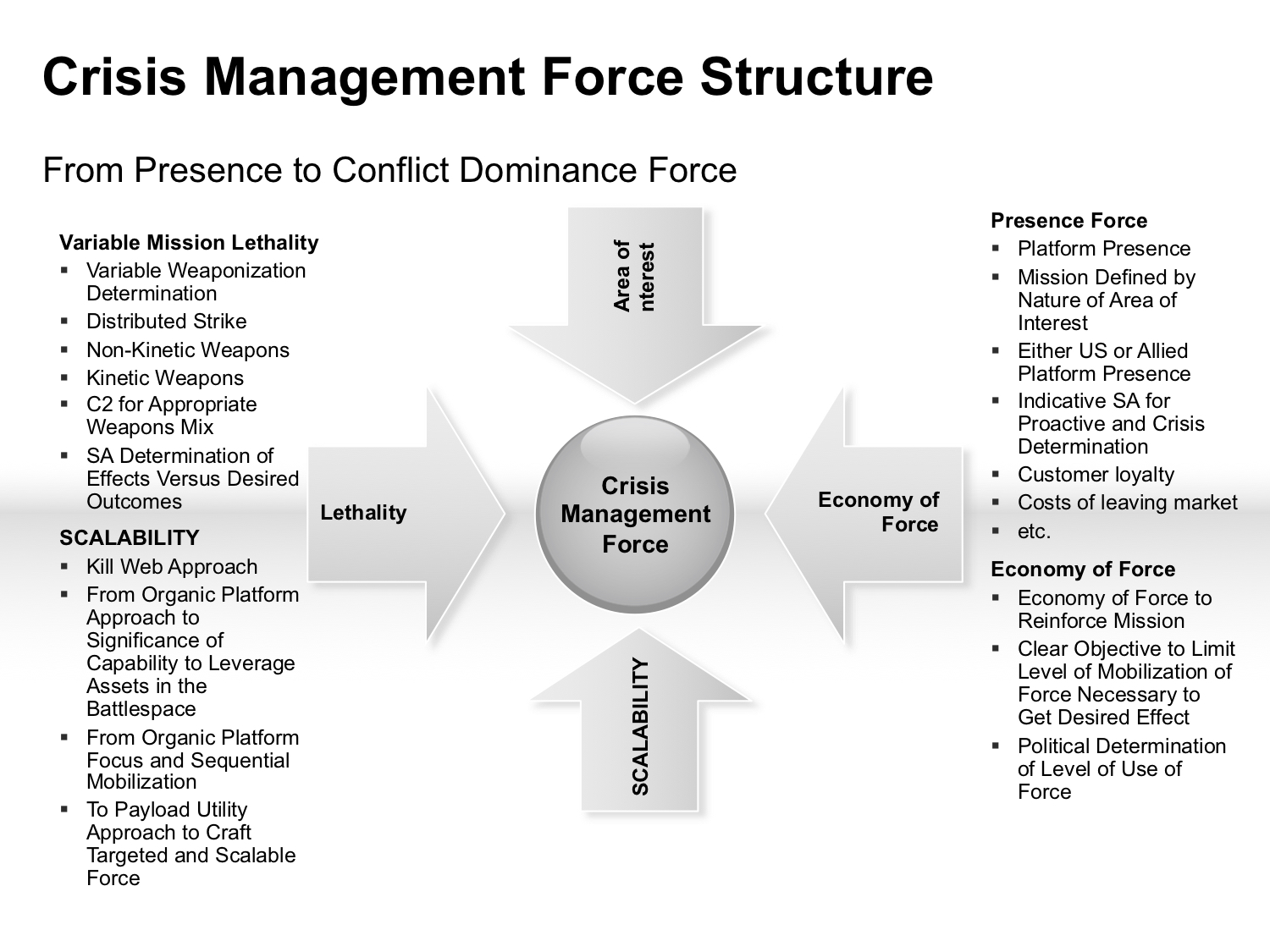
The featured graphic highlights the challenges of shaping a full spectrum crisis management force.
It is clear that economy of force, scalability and agrability of force to dominate escalation management is crucial.
To shape such an integrated distributed force, clearly multi-domain C2/ISR integratability is a central enabler.