The Evolution of C2: The Perspective of Marja Phipps, Cubic Corporation
Recently, I had a chance to talk with an industry leader with regard to the evolution of C2 and ISR infrastructure.
Marja Phipps currently is business development director for Cubic Mission Solutions (CMS), a business division of Cubic Corporation.
She has more than thirty year’s experience in the C2 and ISR areas and has lived through the thirty-year development of C2 and ISR with the cycles of innovation changing dramatically to create the new technological situation in which we find ourselves.
She has focused on providing C4ISR system offerings to military services, defense agencies, intelligence community and multinational partners. Her domain expertise includes communications and networking, knowledge-based systems, multi-INT Processing Exploitation and Dissemination tradecraft, and enterprise interoperability.
What she explained is that the earlier concepts of networking relied on hardwired networks, and single point networking solutions. This meant that the network required careful planning and coordination with the particular platforms which were using the networks to get the combat or joint effect from a networked capability.
“Earlier we built a dedicated single network connection for a specific task, such as providing targeting information to the platforms involved in a specific operation.”
The “networked” force was built around platforms that would use networked information to create desired and often scripted events.
But the C2 and ISR revolution we are now facing is reversing the logic of platforms to infrastructure; it is now about how flexible C2 and ISR interactive systems can inform the force elements to shape interactive combat operations on the fly.
That is, the new capabilities are enabling tactical decision making at the edge and posing real challenges to traditional understandings of how information interacts with decision making.
It is about learning how to fight effectively at the speed of light in order to achieve combat dominance.
And these new capabilities are providing a real impact on force development, concepts of operations and force training as well.
“With the new technologies and capabilities, we are now reusing networks for multiple purposes and making sure that they can adapt to the changing con-ops as well.”
“We are seeing integration of the networks and the integration of the information management services and then the dual nature of the applications on top of those integrations.
“Rather than building a single purpose intel common operating picture, we are now capable of building an integrated intelligence and battlespace management common operating picture for the use of the combat forces engaged in operations.”
She argued that there are significant changes at each layer of the C2 and ISR systems becoming increasingly integrated for a distributed force.
“At each layer, we are making the technology more robust. For example, at the communications layer, the connections are more redundant and protected and are data agnostic.
“You don’t have a dedicated network for one piece of data or between specific platforms, you’ve got the ability to network anything essentially.”
In other words, “we are building an adaptable network of networks. In traditional networks, when data is brought in from a dedicated system, it needs to be repurposed for other tasks as needed.”
What the technology is allowing us to do, is to think about C2 and ISR in a very different fashion, and to think in terms of enabling a small force operations or Lego block approach to the buildup of forces.
The new C2 and ISR infrastructure allows one to think about force development differently.
Phipps noted: “Access data points are becoming ubiquitous and operating in conjunction with processing data services which are scalable across a highly redundant protected communications network.”
“We are putting communications capabilities understood in terms of being able to operate with scalable processing and data services at the tactical edge.
“The edge players are becoming key players in the decision making involving the distributed force.
“They are not just sending data back but they are making decisions at the tactical edge.
“The network gives you the access to not only the ISR data, but the C2 processes as well. The targeting data can be repurposed as well for additional decision-making, not just at the edge but back into the larger combat enterprise.”
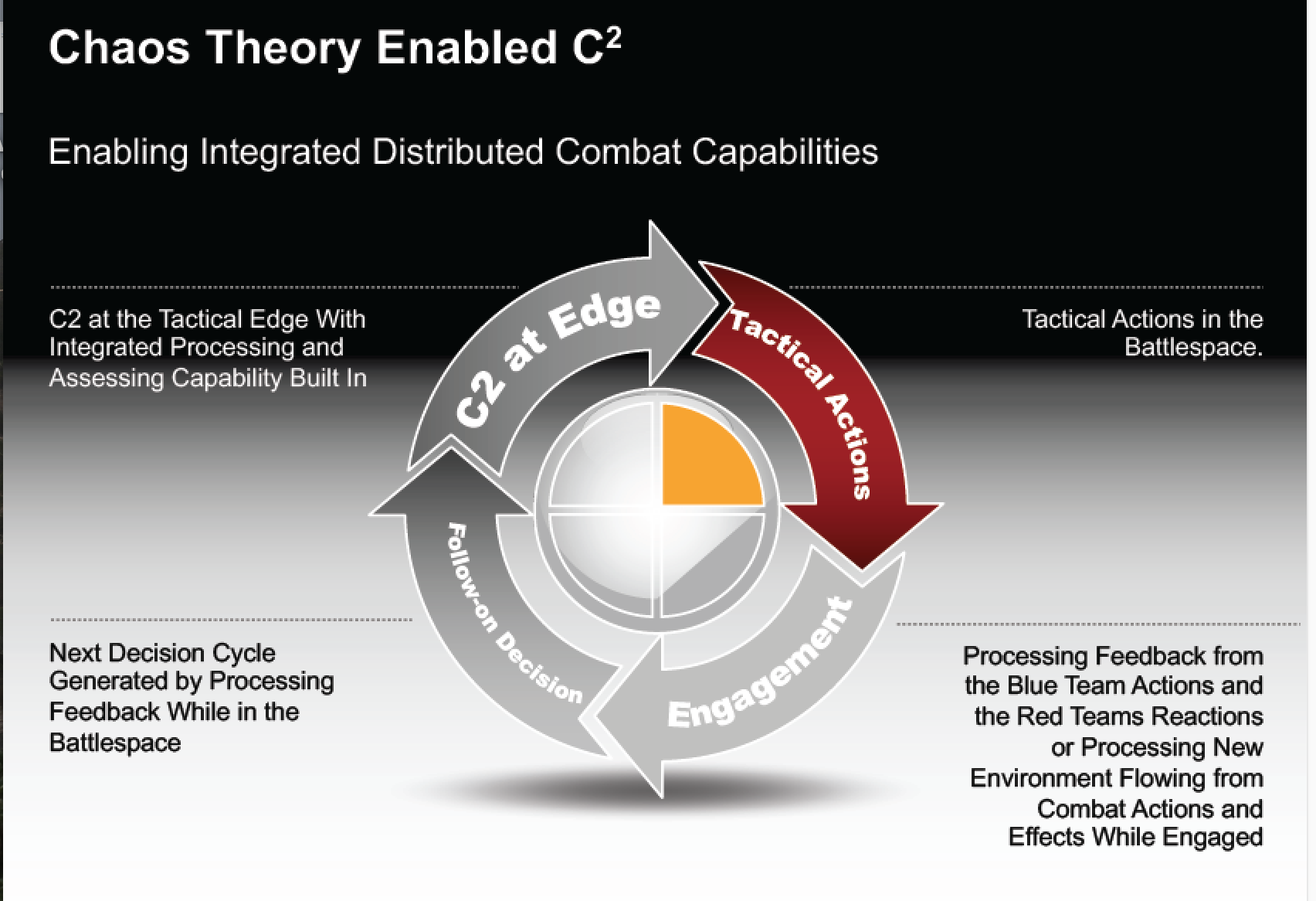
This obviously requires rethinking considerably the nature of decision making and the viability of the classic notion of the OODA loop.
If the machines are fusing data or doing the OO function, then the DA part of the equation becomes transformed, notably if done in terms of decision making at the tactical edge.
The decisions at the edge will drive a reshaping of the information about the battlespace because actors at the tactical edge are recreating the information environment itself.
In effect, chaos theory becomes a key element of understanding of what C2 at the tactical edge means in terms of the nature of the fleeting information in a distributed combat space itself.
“With the new technologies, what you are calling the new C2 and ISR infrastructure enables new warfighting approaches which need to be shaped, exercised and executed, and in turn affect how our forces train for the high-end fight.”
She underscored a key difference from the earlier phase of network centric warfare.
“I think of net-centric as a hardwired con-ops. I think it’s preplanned. You can do it, but there’s no adaptability, there’s no protection, there’s no scalability as far as those architectures were concerned.
“Now we’re going to the next step where we’re making networks adaptable and scalable so that you can essentially re-plan on the fly and make decisions differently, in a distributed manner.
“It’s not a preplanned or scripted way of operating anymore.”
She went on to argue that the focus needed to be going forward on what she called “smart network management.”
What she highlighted is the importance of what might call information parsimony, or getting the right information, to the right person, at the right time.
One of the challenges facing analysts discussing networks is that assumption that too much information is being collected and data is overwhelming the human decision maker. If that is the case, then we are talking about bad network architecture and information management.
She focused on how the key layers in the modern approach to networking interact with one another.
“In an adaptive network of networks, there are several layers interacting dynamically with one another, from a comms layer, to a data processing layer, to a data distribution layer with a network management layer able to dynamically provide for information parsimony.”
On the technology side, it is about both hardware and software solutions which are allowing new capabilities to emerge which allow for a smart networking capability to emerge.
“We’re talking about adaptability and upgradeability here. It’s not just about software upgradeability, it’s about hardware changes that allow for more flexible software solutions and more flexible cross-engagement solutions.”
With the new C2 and ISR infrastructure the opportunity to enhance the capabilities of the legacy force are significant.
“One can add information management and decision processes on an airborne platform with a small processing footprintt.
“You could make good decisions on what you do as far as control on that platform versus what you’re doing as far as control on another platform.
“And it’s across domains as well. We should not think of just a certain processing or information management activity taking place on the ground or in the air.
“We’re also talking space as well and figuring out how to basically connect across all those layers and the assets across those layers as well.”
And going forward we will look at new platforms quite differently.
Rather than discussing generations of platforms, with the information and decision-making infrastructure building out an integrated distributed force, we will look at platforms in terms of what they contribute to the overall capability to such a force, rather than simply becoming autistic injections into the force.
Featured Graphic is credited to Second Line of Defense.