Crafting a Network of Networks for a 21st Century Combat Force
Over the past thirty years, the United States and its core allies have gone through three phases of innovation with regard to conventional forces. The first was air-land battle designed for the European theater and executed in the 1991 Iraqi War. The second was the innovations associated with the land wars and the joint force support for COIN operations. The third which is unfolding now is designed to deal with 21st century high intensity operations which can be conducted by peer competitors.
This new phase might be called shaping, exercising and building an integrated distributed force.
This entails interactive technological, force structure and geographical deployment dynamics. We have argued that a new basing structure combined with a capability to deploy and operate an integrated distributed force is at the heart of the strategic shift, and not only in the Pacific.
This is a key part of the effort to shape a full spectrum crisis management capability whose con-ops is shaped to deal with adversary operations within what some call the “gray zone” or within the “hybrid warfare” area.
The nature of the threat facing the liberal democracies was well put by a senior Finnish official: “The timeline for early warning is shorter; the threshold for the use of force is lower.”
What is unfolding is that capabilities traditionally associated with high end warfare are being drawn upon for lower threshold conflicts, designed to achieve political effect without firing a shot.
Higher end capabilities being developed by China and Russia are becoming tools to achieve political-military objectives throughout the diplomatic engagement spectrum.
This means that not only do the liberal democracies need to shape more effective higher end capabilities but they need to learn how to use force packages which are making up a higher end, higher tempo or higher intensity capability as part of a range of both military operations but proactive engagement to shape peer adversary behavior.
In today’s world, this is what full spectrum crisis management is all about. It is not simply about escalation ladders; it is about the capability to operate tailored task forces within a crisis setting – to dominate and prevail within a diversity of crises which might not be located on what one might consider an escalation ladder.
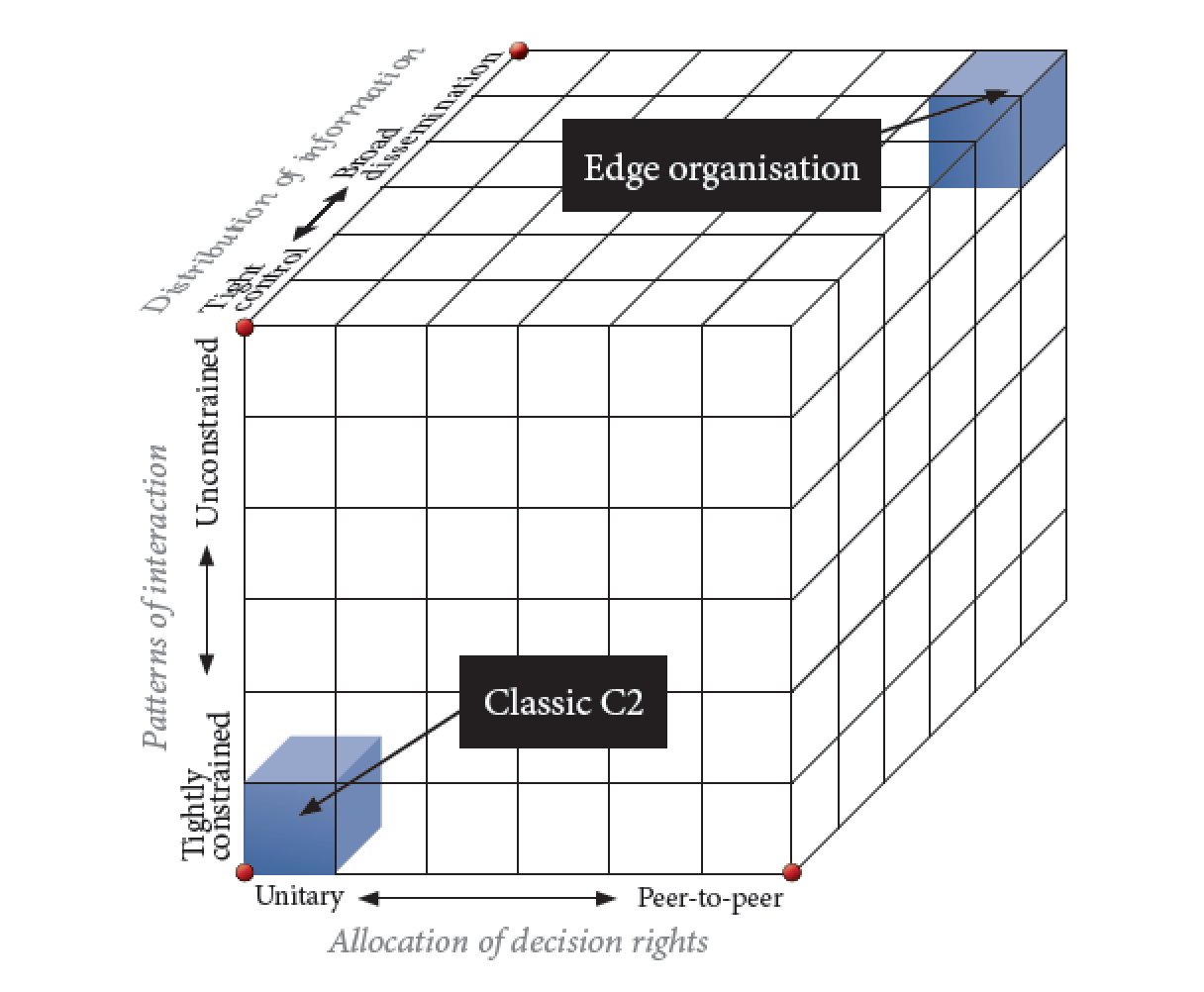
This means that a core legacy from the land wars and COIN efforts needs to be jettisoned if we are to succeed – namely, the OODLA loop. The OODA loop is changing with the new technologies which allow distributed operators to become empowered to decide in the tactical decision-making situation.
But the legacy approach to hierarchical approval to distributed decisions simply will take away the advantages of the new distributed approach and give the advantage to our authoritarian adversaries.
What is changing is that the force we are shaping to operate in the littorals has expansive reach beyond the presence force in the littorals themselves. If you are not present; you are not present. We have to start by having enough platforms to be able to operate in areas of interest.
But what changes with the integrated distributed ops approach is what a presence force can now mean.
Historically, a presence force is about what is organically included within that presence force; now we are looking at reach or scalability of force. We are looking at economy of force whereby what is operating directly in the area of interest is part of distributed force.
The presence force however small needs to be well integrated but not just in terms of itself but its ability to operate via C2 or ISR connectors to an enhanced capability. But that enhanced capability needs to be deployed in order to be tailorable to the presence force and to provide enhanced lethality and effectiveness appropriate to the political action needed to be taken.
This rests really on a significant rework of C2 in order for a distributed force to have the flexibility to operate not just within a limited geographical area but to expand its ability to operate by reaching beyond the geographical boundaries of what the organic presence force is capable of doing by itself.
This requires multi-domain SA. This is not about the intelligence community running its space- based assets and developing reports. This is about looking for the coming confrontation which could trigger a crisis and the SA capabilities airborne, at sea and on the ground that would provide the most usable SA monitoring. This is not “actionable intelligence.” This is about shaping force domain knowledge in anticipation of events.
This also requires tailored force packaging to take advantage of what the new military technologies and platforms can provide in terms of multi-domain delivery by a small force rather than a large air-sea enterprise which can only fully function if unleashed in sequential waves.
This is not classic deterrence – it is about pre-crisis and crisis engagement.
The force we are building will have five key capabilities:
- Enough platforms with allied and US forces in mind to provide significant presence;
- A capability to maximize economy of force with that presence;
- Scalability whereby the presence force can reach back if necessary at the speed of light and receive combat reinforcements;
- Be able to tap into variable lethality capabilities appropriate to the mission or the threat in order to exercise dominance.
- And to have the situational awareness relevant to proactive crisis management at the point of interest and an ability to link the fluidity of local knowledge to appropriate tactical and strategic decisions.
The new approach is one which can be expressed in terms of a kill web, that is a US and allied force so scalable that if an ally goes on a presence mission and is threatened by a ramp up of force from a Russia or China, that that presence force can reach back to relevant allies as well as their own force structure.
A shift to a kill web approach to force building, training and operations is a foundation from which the US and its allies can best leverage the force we have and the upgrade paths to follow.
For this approach to work, there is a clear need for a different kind of C2 and ISR infrastructure to enable the shift in concepts of operations.
Indeed, when describing C2 and ISR or various mutations like C4ISR, the early notions of C2 and ISR seen in both air-land battle and in joint support to the land wars, tend to be extended into the discussions of the C2 and ISR infrastructure for the kill web or for force building of the integrated distributed force.
But the technology associated with C2 and ISR has changed significantly throughout this thirty year period, and the technology to shape a very different kind of C2 and ISR infrastructure is at hand to build enablement for distributed operations.
Recently, I had a chance to talk with an industry leader with regard to the evolution of C2 and ISR infrastructure.
Marja Phipps currently is business development director for Cubic Mission Solutions (CMS), a business division of Cubic Corporation.
She has more than thirty year’s experience in the C2 and ISR areas and has lived through the thirty-year development of C2 and ISR with the cycles of innovation changing dramatically to create the new technological situation in which we find ourselves.
She has focused on providing C4ISR system offerings to military services, defense agencies, intelligence community and multinational partners. Her domain expertise includes communications and networking, knowledge-based systems, multi-INT Processing Exploitation and Dissemination tradecraft, and enterprise interoperability.
What she explained is that the earlier concepts of networking relied on hardwired networks, and single point networking solutions. This meant that the network required careful planning and coordination with the particular platforms which were using the networks to get the combat or joint effect from a networked capability.
“Earlier we built a dedicated single network connection for a specific task, such as providing targeting information to the platforms involved in a specific operation.”
The “networked” force was built around platforms that would use networked information to create desired and often scripted events.
But the C2 and ISR revolution we are now facing is reversing the logic of platforms to infrastructure; it is now about how flexible C2 and ISR interactive systems can inform the force elements to shape interactive combat operations on the fly.
That is, the new capabilities are enabling tactical decision making at the edge and posing real challenges to traditional understandings of how information interacts with decision making.
It is about learning how to fight effectively at the speed of light in order to achieve combat dominance.
And these new capabilities are providing a real impact on force development, concepts of operations and force training as well.
“With the new technologies and capabilities, we are now reusing networks for multiple purposes and making sure that they can adapt to the changing con-ops as well.”
“We are seeing integration of the networks and the integration of the information management services and then the dual nature of the applications on top of those integrations.
“Rather than building a single purpose intel common operating picture, we are now capable of building an integrated intelligence and battlespace management common operating picture for the use of the combat forces engaged in operations.”
She argued that there are significant changes at each layer of the C2 and ISR systems becoming increasingly integrated for a distributed force.
“At each layer, we are making the technology more robust. For example, at the communications layer, the connections are more redundant and protected and are data agnostic.
“You don’t have a dedicated network for one piece of data or between specific platforms, you’ve got the ability to network anything essentially.”
In other words, “we are building an adaptable network of networks. In traditional networks, when data is brought in from a dedicated system, it needs to be repurposed for other tasks as needed.”
What the technology is allowing us to do, is to think about C2 and ISR in a very different fashion, and to think in terms of enabling a small force operations or Lego block approach to the buildup of forces.
The new C2 and ISR infrastructure allows one to think about force development differently.
Phipps noted: “Access data points are becoming ubiquitous and operating in conjunction with processing data services which are scalable across a highly redundant protected communications network.”
“We are putting communications capabilities understood in terms of being able to operate with scalable processing and data services at the tactical edge.
“The edge players are becoming key players in the decision making involving the distributed force.
“They are not just sending data back but they are making decisions at the tactical edge.
“The network gives you the access to not only the ISR data, but the C2 processes as well. The targeting data can be repurposed as well for additional decision-making, not just at the edge but back into the larger combat enterprise.”
This obviously requires rethinking considerably the nature of decision making and the viability of the classic notion of the OODA loop.
If the machines are fusing data or doing the OO function, then the DA part of the equation becomes transformed, notably if done in terms of decision making at the tactical edge.
The decisions at the edge will drive a reshaping of the information about the battlespace because actors at the tactical edge are recreating the information environment itself.
In effect, chaos theory becomes a key element of understanding of what C2 at the tactical edge means in terms of the nature of the fleeting information in a distributed combat space itself.
“With the new technologies, what you are calling the new C2 and ISR infrastructure enables new warfighting approaches which need to be shaped, exercised and executed, and in turn affect how our forces train for the high-end fight.”
She underscored a key difference from the earlier phase of network centric warfare.
“I think of net-centric as a hardwired con-ops. I think it’s preplanned. You can do it, but there’s no adaptability, there’s no protection, there’s no scalability as far as those architectures were concerned.
“Now we’re going to the next step where we’re making networks adaptable and scalable so that you can essentially re-plan on the fly and make decisions differently, in a distributed manner.
“It’s not a preplanned or scripted way of operating anymore.”
She went on to argue that the focus needed to be going forward on what she called “smart network management.”
What she highlighted is the importance of what might call information parsimony, or getting the right information, to the right person, at the right time.
One of the challenges facing analysts discussing networks is that assumption that too much information is being collected and data is overwhelming the human decision maker. If that is the case, then we are talking about bad network architecture and information management.
She focused on how the key layers in the modern approach to networking interact with one another.
“In an adaptive network of networks, there are several layers interacting dynamically with one another, from a comms layer, to a data processing layer, to a data distribution layer with a network management layer able to dynamically provide for information parsimony.”
On the technology side, it is about both hardware and software solutions which are allowing new capabilities to emerge which allow for a smart networking capability to emerge.
“We’re talking about adaptability and upgradeability here. It’s not just about software upgradeability, it’s about hardware changes that allow for more flexible software solutions and more flexible cross-engagement solutions.”
With the new C2 and ISR infrastructure the opportunity to enhance the capabilities of the legacy force are significant.
“One can add information management and decision processes on an airborne platform with a small processing footprintt.
“You could make good decisions on what you do as far as control on that platform versus what you’re doing as far as control on another platform.
“And it’s across domains as well. We should not think of just a certain processing or information management activity taking place on the ground or in the air.
“We’re also talking space as well and figuring out how to basically connect across all those layers and the assets across those layers as well.”
And going forward we will look at new platforms quite differently.
Rather than discussing generations of platforms, with the information and decision-making infrastructure building out an integrated distributed force, we will look at platforms in terms of what they contribute to the overall capability to such a force, rather than simply becoming autistic injections into the force.
Editor’s Note: The featured graphic was taken from Lt. Col. Bart A. Hobein’s study entitled 5th Generation Air and ISR.
FELL39-5th-Generation-C2-and-ISR