The Way Ahead for C2 for a 21st Century Combat Force: Challenges and Opportunities
Over the past thirty years, the United States and its core allies have gone through three phases of innovation with regard to conventional forces.
The first was air-land battle designed for the European theater and executed in the 1991 Iraqi War.
The second phase was the significant shift associated with the land wars and the joint force support for COIN operations.
The third which is unfolding now is designed to deal with 21st century high intensity operations which can be conducted by peer competitors.

And to be blunt about it – the capabilities and the infrastructure for such an approach with regard to C2 are radically different.
Yet the same acronym C2 is used.
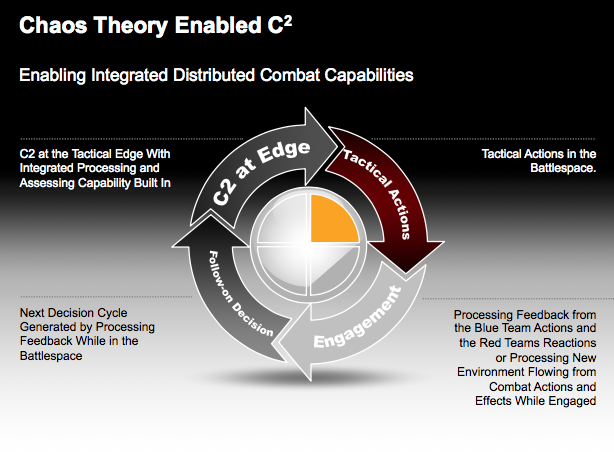
How might we conceptualize the nature of the C2 required to empower the integrated distributed force?
Crafting an Integrated Distributed Force
This new phase might be called shaping, exercising and building an integrated distributed force.
This entails interactive technological, force structure and geographical deployment dynamics.
This is a key part of the effort to shape a full spectrum crisis management capability whose con-ops is shaped to deal with adversary operations within what some call the “gray zone” or within what has been labelled by some as the “hybrid warfare” engagement area.
The nature of the threat facing the liberal democracies was well put by the Finnish Ministry of Defence: “The timeline for early warning is shorter; the threshold for the use of force is lower.”
What is unfolding is that capabilities traditionally associated with high end warfare are being drawn upon for lower threshold conflicts, ones that are designed to achieve political effect without firing a shot.
Higher end capabilities being developed by China and Russia are becoming tools to achieve political-military objectives throughout the diplomatic engagement spectrum.
This means that not only do the liberal democracies need to shape more effective higher end capabilities but they need to learn how to use force packages which are making up a higher end, higher tempo or higher intensity capability as part of a range of both military operations but proactive engagement to shape peer adversary behavior.
In today’s world, full spectrum crisis management is not simply about escalation ladders; it is about the capability to operate tailored task forces within a crisis setting to dominate and prevail within that crisis. If that stops the level of escalation that is one way of looking at it.
But in today’s world, it is also about the ability to operate and prevail within a diversity of crises which might not be located on what one might consider an escalation ladder.
This means that a core legacy from the land wars and COIN efforts needs to be jettisoned if we are to succeed – namely, the OODLA loop. The Observe-Orient-Decide-Lawyer-Act loop is to slow to make decisions at the tactical edge in the evolving world of combat.
The OODA loop is changing with the new technologies which allow distributed operators to become empowered to decide in the tactical decision-making situation.
But the legalistic approach to hierarchical approval to distributed decisions simply will take away the advantages of the new distributed approach and give the advantage to our authoritarian adversaries.
What changes with the integrated distributed ops approach is what a presence force can now mean.
Historically, the presence force has been about what organically can be included within that presence force; now we are looking at reach or scalability of a force operating in terms of its effects on an area of interest.
Economy of force is a key attribute of a scalable force as well.
The presence force, however small, needs to be well integrated but not just in terms of itself but its ability to operate via C2 or ISR connectors to an enhanced capability.
But that enhanced capability needs to be deployed in order to be tailorable to the presence force and to provide enhanced lethality and effectiveness appropriate to the political action needed to be taken.
This rests really on a significant rework of network accessibility for C2 in order for a distributed force to have the flexibility to operate not just within a limited geographical area but to expand its ability to operate by reaching beyond the geographical boundaries of what the organic presence force is capable of doing by itself.
This requires multi-domain situational awareness (SA) – this is not about the intelligence community running its precious space- based assets and hoarding material.
This is about looking for the coming confrontation which could trigger a crisis and the SA capabilities airborne, at sea and on the ground would provide the most usable SA monitoring.
This is not “actionable intelligence.”
This is about shaping force domain knowledge to anticipate events.
What is required is tailored force packaging and an ability to take advantage of what the new military technologies and platforms can provide in terms of multi-domain delivery by a smaller force rather than a large air-sea enterprise which can only fully function if unleashed in sequential waves.
It is clear that connectivity for a distributed force is a foundational element; it is also clear that such connectivity must be secure and able to operate in peer-to-peer conflict and is capable of being multi-domain and operated by air, sea and ground elements in an interactive and distributed combat environment.
But it is equally clear that we are not talking about traditional C2 as understood in the world of legacy combat radios or as evidenced in the period of the land wars.
We are talking about being able to operate at the speed of light, and to make decisions at the tactical edge and to do so while engaged in operations and to generate responses while still engaged, rather than relying on reachback intelligence evaluators and decision makers.
C2 for the Integrated Distributed Force
There is a significant dynamic of change in the world of C2 systems which is reshaping capabilities which can allow decision makers within distributed task force elements to combine their capability into an integratable combat capability.
First, there is no single road in existence or being built down which the platforms can “drive” to reach the convergent point of operation.
There are multiple highways, some paved, some dirt roads, and some being considered by force planners for future development.
This means that various platforms tap into various networks to generate the information based upon which decisions are made.
But which networks deliver the best information, at the right time for the most effective actions?
Platforms operating across the battlespace leverage networks which provide their operators with the information they deem most accurate to make their decisions.
Second, this gets at a key aspect of C2 which is not about the networking systems themselves, but the operational experience and training of the operators in the integrated force about how best to work together.
Within a task force, operators on various platforms will shape combat experience and training which will determine how they are relied upon to make decisions for the broader integrated task force.
It is about levels of confidence in the data coming from various networks that decision makers will then proceed to act.
Third, there is a growing capability for machine-to-machine communication which handles data and generates data into information.
Artificial intelligence and machine to machine communication are clearly growing in importance, but the challenge is to manage information flows to ensure that information inputs do not slow down decision-making capabilities.
How then best to manage machine-to-machine communications into an effect C2 process?
And how to handle the spoofing which adversaries will work to inject into the machine-to-machine networking world?
Fourth, there is the clear challenge of communication and information security.
Cyber war and cyber operations are clearly part of the challenge, but another part of the equation is how to ensure that forces working to shape an integrated force capability have the ability to work with a diversity of forces with the appropriate security caveats.
This is especially significant when working across the spectrum of conflict to manage a crisis.
There may be a clear need to work with civilian organizations, higher end combat forces, to deliver sensitive political and combat decision making options through the networks which need to be funneled into a decision-making point, which could be at the tactical edge or in a C2 center.
Notably, on the new aircraft carriers, such as the USS Ford and HMS Queen Elizabeth there are a number of C2 rooms which can be stood up in a crisis, which can allow for different organizational outreach to be worked from the ships.
Fifth, new civilian systems are coming into play which dwarf the investments in military systems and will shape capabilities which will be more capable than strictly military systems and will access parts of the communications spectrum which impede their use by military systems.
Clearly, the coming of 5G, for example, will have a major impact on the networks which will be used for crisis management C2.
Characterizing the Challenge
At last Fall’s Williams Foundation seminar which looked at C2 for an integrated distributed force, the noted Australian strategist, Michael Shoebridge characterized the challenge facing the ADF as it continued its force transformation.
The transitory, small 5th Generation bubble of force projection and force protection provided by platforms like the F-35, P-8s and Growlers are extremely valuable, but the bulk of the ADF, Defence organisation, defence industry and ‘national support base’ do not have these advantages and are vulnerable to the cyber, kinetic and information domain attacks that can disable and confuse the deployed force and its decision makers.
The problem is not encrypting or securing SATCOM between nodes and platforms, it’s being able to operate without such nodes and connections. This requires a force design approach that can unite and disaggregate easily.
On this dispersal and disaggregation, I think Orwell’s Animal Farm has a useful principle: “Some animals are more equal than others.” Some platforms and people will be able to be – and need to be – ‘super users’ of data and analytic tools and skills. These will be the deployed ‘disaggregated brains’ of the forming and reforming temporary networks force design needs to create.
A super user may turn out to be a Wedgetail or P-8, which has a critical mass of sensors, people and processing hardware to cache large data sets and turn them into decisions and operational activities. But these large, vulnerable nodes won’t be sufficient operational ‘super users’, because they won’t be connected enough to at risk deployed people and systems deeper in the threat environment.
So, platforms like Growler and the F-35, which are ‘super collectors’ already, must become sup users, who carry wider data sets and who are enabled by more powerful artificial intelligence and processing than currently imagined, and who can themselves act on the results in ways probably not authorised now.
And autonomous systems need to be in this chain at higher or lower levels depending on their role. Maybe some are data and data analytic trucks who can connect to other force elements but be lost and replaced.
I hate the term, but a very different ‘data and communications architecture’ and ‘command and control architecture’ is needed in this world.
In my terms, what Shoebridge is calling for is shaping and empowering a C2 infrastructure to allow a scalable force with a diversity of force packages tailored to a crisis to form, operate and be able to reachback to additional combat capabilities as needed in a crisis.
This is the C2 “engine’s” ability to shape a combat force something along the line of a configurable Lego block operational force.
It is the C2 infrastructure which is at the heart of forging a mixable force, tailored to a crisis but capable of reaching back to the kind of combat or crisis response management capabilities needed to achieve force equilibrium or dominance.
At the Chief of Navy Seapower Conference held in Sydney last October, the Chief of Navy’s panel had two presentations which highlighted two different aspects of the Lego block challenge which can be enabled by an appropriate C2 infrastructure.
Vice Admiral Johnston, Deputy Chief of the ADF, argued that the ADF was seeking advantages over its adversaries in terms of knowledge of the environment, an ability to draw together different parts of a joint or coalition force to get the kind of combat effects desired, and to be able to operate more quickly and decisively than the adversaries.
In effect, what he identified was the need for the ADF to have a C2/ISR infrastructure which enabled the scalable force to operate effectively in a timely manner.
He then added: “With our small force we need to need to focus on how to generate the appropriate mass and scale for that force to achieve the combat effects we need.”
That clearly rests on a C2 approach which allows both the ADF and the coalition partners to work together.
And that would rest on not just having something like a high-end F-35 CNI capability, but upon a distributed and diffused capability, and one which can leverage what the F-35 brings to the force,
The scalability aspect also highlights the importance of the ability to manage several levels of security on the fly, quite literally.
It is not just the case that the ADF or the U.S. will operate with the five eyes partners; coalitions will need to be organized lego block-like into a combat force led by either the coalition partner or the United States.
That is not going to happen without the right kind of C2/ISR infrastructure.
Put bluntly, C2 systems are no longer commodities added platform by platform; they are the operating infrastructure within which platforms find their role within a scalable, tailorable combat force.
This is a major reversal from both the first and second phases of conventional modernization in my lifetime.